Cloud Security and Compliance for Energy & Utilities Sector

As cloud adoption gains momentum in the energy and utilities sector, it is important for CIOs & CISOs to understand the security and compliance implications of cloud migration. Cloud services are often delivered over the public internet, which exposes it to several risks that need to be considered. To address this, it is important for energy and utilities companies to perform due diligence when selecting a cloud service provider, and put in place the necessary security controls to protect their data and applications.
In this article, we will discuss the challenges and best practices to keep in mind when it comes to cloud security and compliance for energy and utilities companies.
The ever-increasing importance of cloud
Spurred on by strictures imposed by the Covid-19 pandemic, cloud migration has accelerated at an unprecedented pace in recent months. A report by research firm Canalys shows that public cloud services revenue grew by 29% in the first quarter of 2021, with AWS, Microsoft Azure, and Google Cloud Platform (GCP) leading the pack.
The global importance of cloud computing can be seen in market growth alone, with the cloud computing market, valued at $371.4 billion in 2020, set to reach a staggering $832.1 billion by 2025.
The energy and utilities sector is no exception to this trend – a recent study by Deloitte shows that 83% of energy and utilities companies are currently using or plan to use cloud services within two years. Cloud usage in the energy and utilities sector is driven by several factors, including the need for improved agility and flexibility, reduced capital expenditure (CapEx) costs, and increased operational efficiency.
However, as organizations continue to migrate their workloads to the cloud, it is important to consider the security and compliance risks involved. Failure to do so could result in data breaches, loss of customer trust, and reputational damage.
The good news is that there are a few steps that energy and utilities companies can take to mitigate these risks and ensure that their cloud environments are secure and compliant.
What are the cloud migration challenges facing the energy and utilities sector?
There is a range of challenges that energy and utilities companies need to consider when migrating workloads to the cloud. These can be broken down into three brackets - compliance, security, and organizational.
Ensuring compliance
One of the key challenges associated with migrating to the cloud is ensuring compliance with industry regulations. The energy and utilities sector is subject to a number of stringent national regulations, such as Sarbanes-Oxley (SOX), the Gramm-Leach-Bliley Act (GLBA), and the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP).
Organizations must ensure that their Cloud Service Provider (CSP) can meet all the necessary compliance requirements before migrating any workloads.
Data security
Another challenge that needs to be considered is data security. The energy and utilities sector deals with a large amount of sensitive data, such as customer information and confidential business data. Hence, it’s essential that this data is protected from unauthorized access, and is only accessible to authorized personnel as data breaches are a serious concern for organizations in this sector and can have a major impact on their business.
In order to protect data, organizations need to implement security measures, such as data encryption, access control, and intrusion detection and prevention. Organizations should also consider using a cloud security platform that provides comprehensive security for their workloads.
The Cloud Security Alliance’s Cloud Controls Matrix (CCM) is a good starting point for understanding the security controls that need to be in place.
Organizational issues
Organizational issues, such as data governance, compliance, and risk management must also be considered when migrating workloads to the cloud. Cloud service providers should be selected based on their ability to meet the specific security and compliance requirements of the organization.
It is also important to note that migrating to the cloud does not absolve an organization of its responsibility for ensuring security and compliance. Cloud service providers will typically have all the security controls in place, but it is the responsibility of the organization to ensure that these controls meet their specific requirements.
Some of the more common organizational issues include:
Outdated systems
One of the key challenges facing organizations in the energy and utilities sector is that many legacy systems were not designed with security in mind. Legacy systems often use proprietary protocols and standards that are not compatible with modern security tools and technologies. This makes it difficult to implement or deploy effective security controls / solutions in a cloud environment.
In addition, many legacy systems were not designed to be accessed remotely, which disabled the ability to securely connect to them from a cloud environment.
Defining roles and responsibilities for security in the cloud
In a traditional on-premises environment, responsibilities are typically clearly defined when it comes to security. However, in a cloud environment, there may be multiple stakeholders involved in providing security, including the customer, the cloud service provider, and third-party vendors.
In such cases, it can be difficult to determine or define who is responsible for securing which assets in the cloud. For example, is the customer responsible for securing their data, or is that the responsibility of the cloud service provider?
To complicate matters further, many organizations use a hybrid approach, with some workloads running on-premises and others in the cloud. This can make it even more difficult to understand and manage security risks.
Establishing processes and procedures for managing security in the cloud
Cloud service providers typically have security controls in place to protect their infrastructure and services. However, these controls may not be sufficient to meet the specific requirements of your organization.
Thus, it is important to, first, understand the security controls that are in place and then, how they map to your organization's needs. Additionally, you should also have the required processes and procedures in place to manage security risks.
What are some of the best practices for migrating workloads to the cloud?
While some of the challenges discussed above may seem daunting, there are a few best practices that can help make migrating to the cloud a smoother process. These can again be broken down into compliance, security, and organizational best practices. Let us discuss these in detail.
Compliance
- Define compliance requirements early in the migration process - This will ensure that you select the right cloud provider and configure your environment correctly and securely.
- Work closely with your cloud provider – Your cloud provider will not only have expertise in meeting specific compliance requirements, they can also advise you on how to best configure your environment. Remember to keep cloud security and compliance a shared responsibility between you and your cloud provider. Work with them to ensure that you have the necessary controls in place to protect your data and meet compliance requirements.
- Ensure that you have visibility into all activity in your environment - A holistic cloud security posture is essential for compliance as it helps to identify risks and potential vulnerabilities.
- Use automation to help manage and monitor compliance - This can free up time and resources that can be better spent elsewhere while also providing enhanced security. Automating cloud security and compliance can help to improve your organization's overall posture, making it easier to meet compliance requirements. Automation can also play a major role in simplifying and streamlining these processes. Leveraging Infrastructure-as-Code (IaC), additionally and specifically, can ensure continuous compliance.
The energy and utilities sector is one of the most heavily regulated industries in the world. Cloud security and compliance are therefore critical considerations for companies in this space. By following the best practices outlined above, you can ensure that your migration to the cloud is seamless and successful.
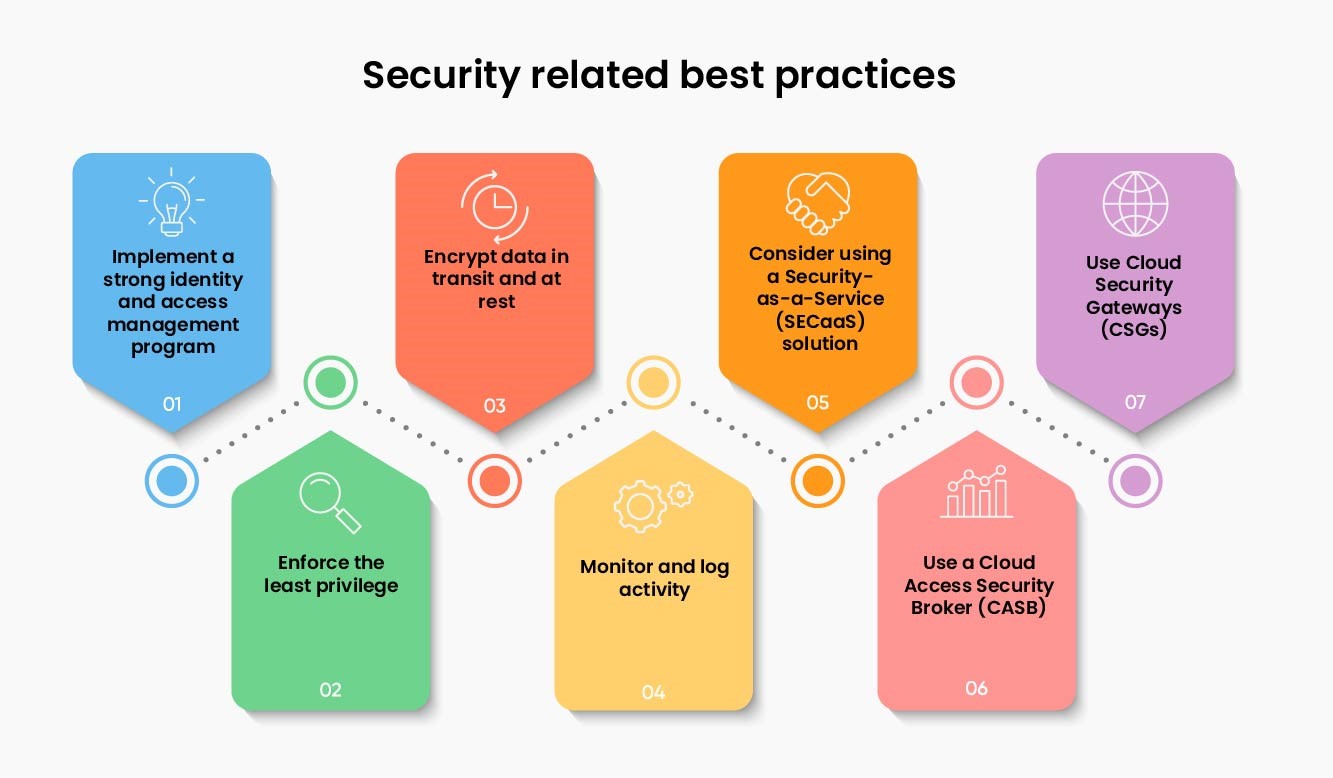
Top 7 best practices to ensure security
1. Implement a strong identity and access management program - An access management program is the foundation for a comprehensive security strategy in the cloud. Thus, it is critical to have a robust system in place to manage user identities, permissions, and roles.
2. Enforce the least privilege - Granting users the minimum amount of access they need to do their job is a key principle of security in the cloud. By doing so, you can reduce the risk of data breaches and other security incidents.
3. Encrypt data in transit and at rest - Data encryption is a key security measure that can help protect your data from unauthorized access. When data is encrypted, it is scrambled so that only authorized users with the proper decryption key can read it.
4. Monitor and log activity - Monitoring and logging activity in the cloud can help you detect unusual or suspicious activity. By tracking activity, you can also identify trends and patterns that may indicate a security concern / issue.
5. Consider using a Security-as-a-Service (SECaaS) solution - A Security-as-a-Service (SECaaS) solution can help you manage and secure your cloud environment. These solutions are typically delivered through the cloud, so they can be easily scaled to meet your specific needs.
6. Use a Cloud Access Security Broker (CASB) - A CASB is a software platform that sits between an organization’s on-premises security infrastructure and its cloud applications. Organizations should consider using a CASB to help them secure their legacy systems in the cloud.
It provides a central point of control for managing security in the cloud, allowing organizations to use their existing security tools and technologies to secure their data in the cloud.
7. Use Cloud Security Gateways (CSGs) - Organizations should also consider using Cloud Security Gateways (CSGs) to secure their data in the cloud. CSGs are hardware or software appliances that act as a gateway between an organization’s on-premises network and their Cloud Service Provider's (CSP) network. They provide a single point of control for managing security and compliance in the cloud.
CSGs can be used to monitor and control traffic between an organization’s on-premises network and their CSP's network. They can also be used to enforce security policies, such as data loss prevention (DLP) policies. CSGs can be deployed in a variety of ways, including on-premises, in the cloud, or as a hybrid solution.
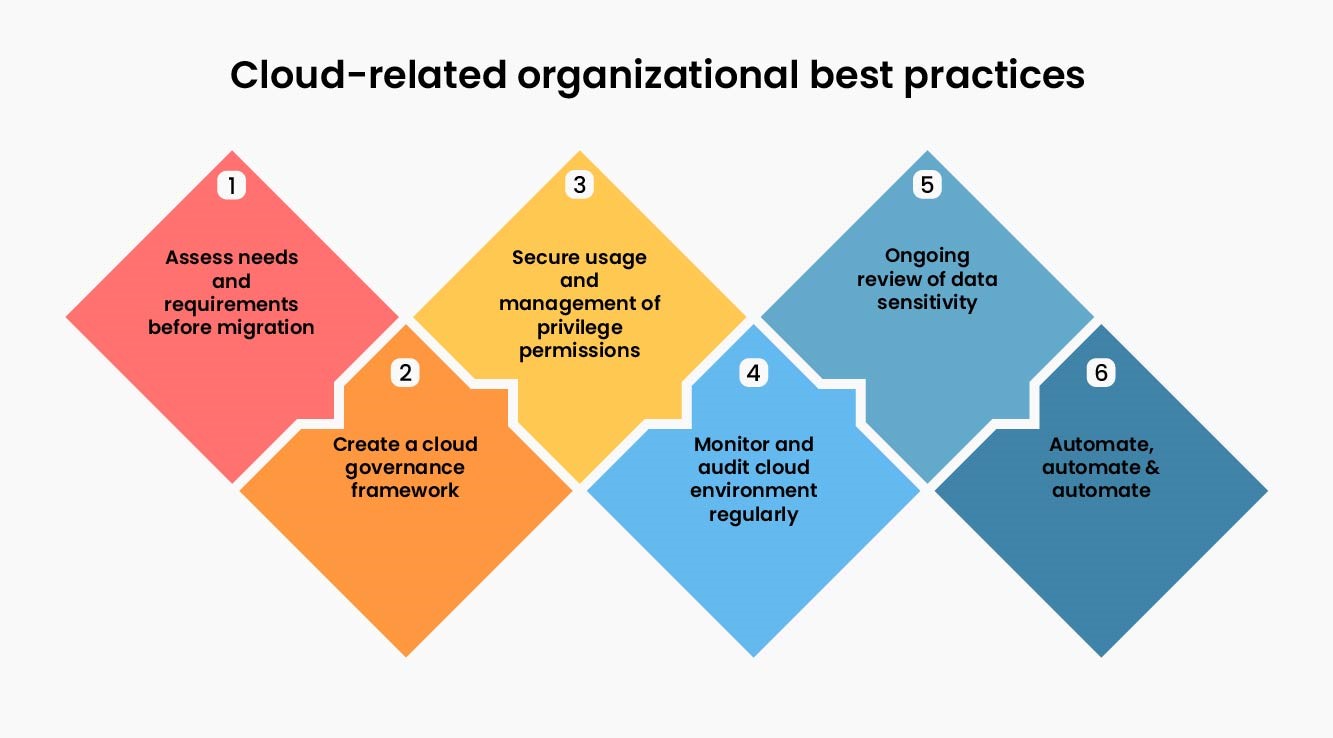
Top 6 cloud-related organizational best practices
1. Thoroughly assess your organization's needs and requirements before beginning the migration process - This will help you determine which workloads are best suited for the public cloud, and which should remain on-premises.
2. Create a cloud governance framework - This will help you establish controls and standards based on the public cloud usage by your organization. A comprehensive governance framework should include cloud security standards, supporting guidelines, and baseline guard rails. The framework defined should also be reviewed and updated on a regular basis.
3. Ensure secure usage and management of privilege permissions - Ensure doing Identity & Access Management using Single Sign On (SSO) capabilities, and the allocation of roles and permissions on a need-to-know basis.
4. Monitor and audit your cloud environment on an ongoing basis - Cloud environments are dynamic and can change quickly. Hence, it is important to monitor and audit your environment on a regular basis to ensure that it remains secure and compliant. Infrastructure-as-Code (IaC) can be of great help here in terms of continuous detection of insecure configuration and vulnerabilities.
5. Ongoing review of data sensitivity - A review of the data sensitivity labels (tags) assigned to cloud workloads is crucial. This is to ensure that appropriate and proportionate security controls are assigned by default to all provisioned cloud workloads, resources, systems, and applications basis these tags.
6. Automate, automate & automate - Deploy auto-healing systems that are capable of automatically remediating identified misconfigurations. Automated deployment of workloads leveraging Infrastructure-as-Code (IaC) via a continuous integration and deployment (CI/CD) pipeline ensures that code-level security assessment and verifications are done for secure, immutable, and repeatable deployments.
By implementing these organizational best practices, you can ensure that your cloud environment is secure and compliant. Energy and utilities public cloud providers are subject to a variety of regulations, so it is important to establish an organizational process and structure for managing compliance.
How to ensure an effective, compliant, and secure Cloud?
Cloud security and compliance is a complex issue that organizations in the energy and utilities sector need to consider carefully.
Energy and utilities companies face unique challenges on a regular basis when it comes to public cloud adoption. While on one hand, they must meet stringent regulatory requirements, on the other hand, they need to take advantage of the agility and cost savings that the public cloud can offer.
By implementing the best practices for cloud security and compliance, energy and utilities companies can reap the benefits of the public cloud while protecting their own and their customers’ data. In our experience, leveraging Infrastructure-as-Code (IaC) based automation can help speed up this process.
Further Reading
AWS for improved IT infrastructure availability for a leading energy and gas provider