Network Integration at the Core of Mergers and Acquisitions

Mergers, Acquisitions, and Divestitures represent fundamental business transactions primarily centered around expanding business capabilities, entering new markets and geographic regions, enhancing product and service portfolios, diversifying revenue streams, extending brand reach, and addressing cultural alignment, among other factors. Regrettably, technological considerations are frequently overlooked during the Mergers and Acquisitions (M&A) process.
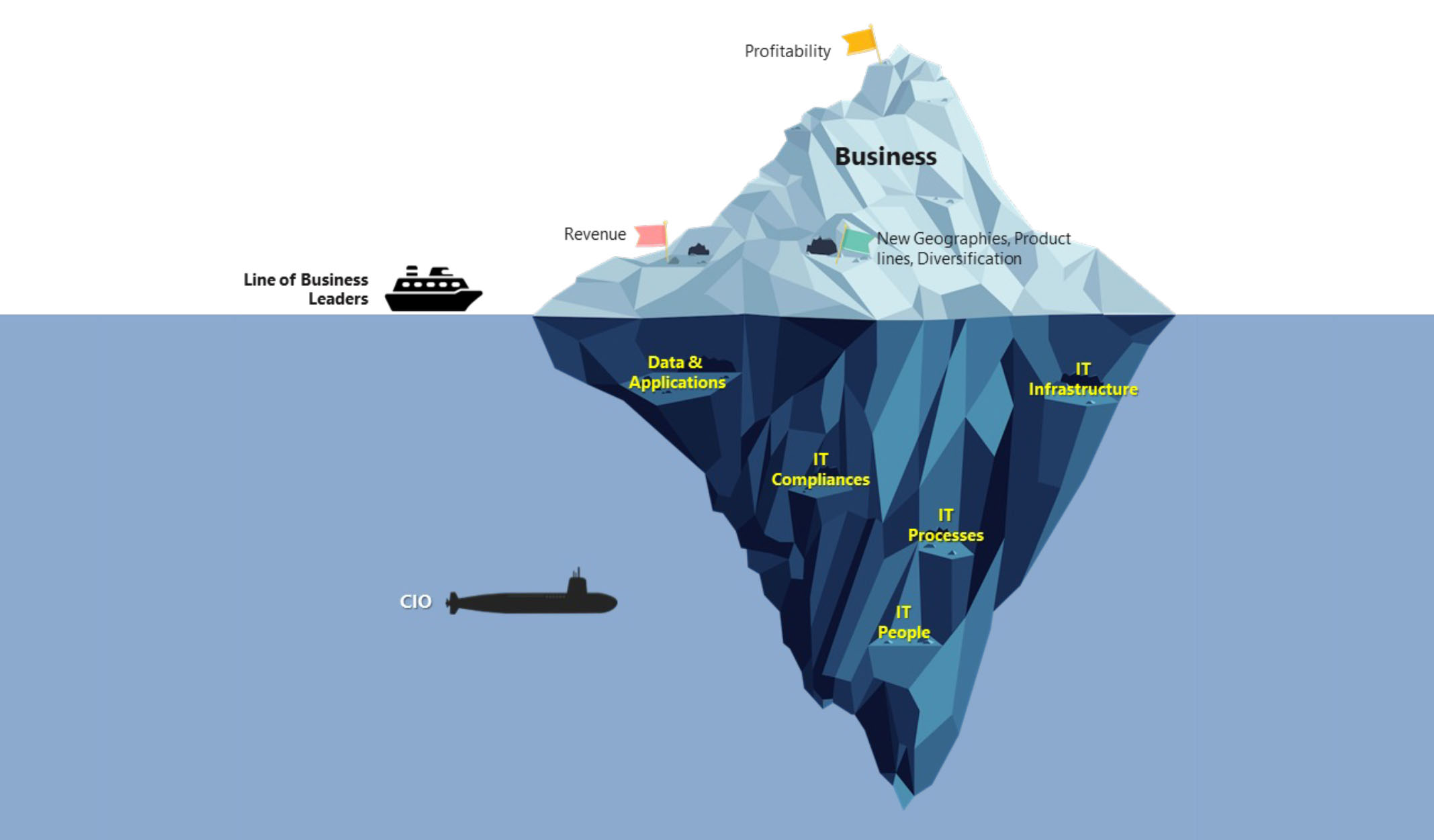
In contrast to earlier times, every company now incorporates technology into its operations, regardless of the industry it belongs to. Today, there are various technological elements to consider, including business and IT applications, ERP systems, databases, networks, security measures, and internal systems associated with various business functions such as HR, Sales, Finance, and Procurement. These elements necessitate integration and optimization as part of the Mergers and Acquisitions process. [A iceberg with a submarine in the background Description automatically generated] Historically, it has been observed that technology, despite being one of the large cost components in an M&A, is often underestimated. This is one of the key reasons for Mergers and Acquisitions not delivering the expected levels of business outcomes or delays in achieving expected business outcomes.
Involving CIOs and IT leaders early in the M&A process allows CIOs to explain the implications and risks associated with IT, leading to better target screening and decision-making. Involving CIOs in the due diligence process also allows for better technology valuation, integration planning, and setting the right expectations in terms of achievable outcomes and timelines.
Irrespective of the depth & variety of challenges and multiple technology elements, the starting point is usually the network. Network connectivity is the string that brings together the complete IT ecosystem.
Network Integrations in M&A
In this blog, we will focus on the approach and best practices towards moving to a unified, secure network as part of M&A and follow up with turning up a new global network & associated services as part of divestiture and spin-offs in the 2nd part.
Every merger and acquisition necessitates IT integration, with a crucial component being the consolidation of the separate IT networks of both entities. Network integration during M&A can be categorized broadly into two distinct groups.
- Complete merger – The two companies are completely integrated into every aspect of technology, services, processes, and people.
- Partial merger – These are scenarios where one or multiple business units of an enterprise are acquired by another enterprise. In such a scenario, before the integration is initiated the acquired business units must be divested in terms of technology, services, and processes.
In both categories, the integration needs to be done keeping in mind business objectives without compromising security, accessibility to applications, and user experience. This activity needs to be cognizant of the budget, Technical Services Agreement (TSA), and timelines.
Another key aspect is to ensure that interim communication channels and networks are implemented to ensure that business operations are not impacted during the integration process.
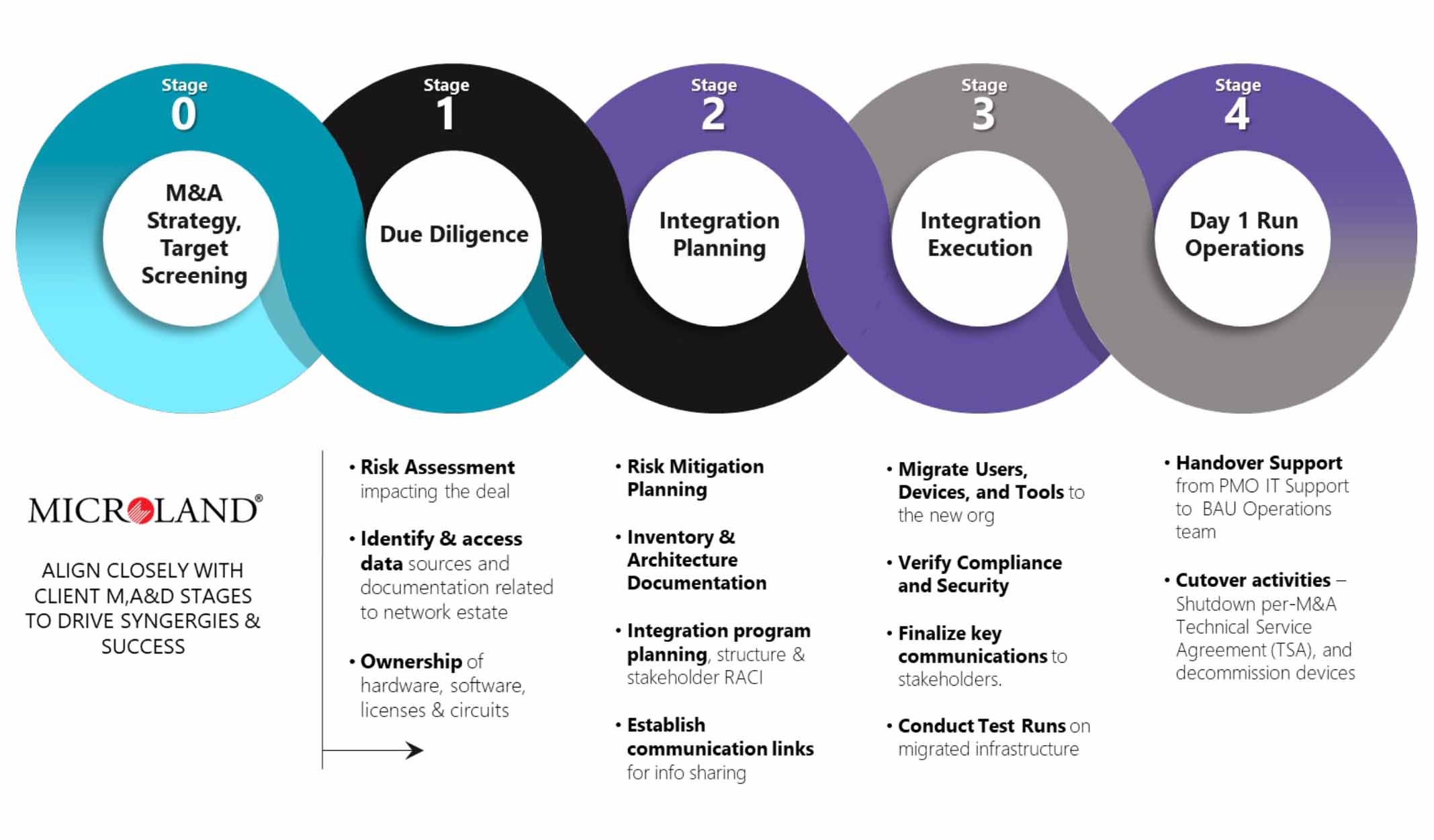
Usually, integration is a massive exercise requiring collaboration among multiple stakeholders aligned to a strategic and structured plan. We have split the activities into multiple stages with success factors defined and measured at each stage.
Stage 0 – At this stage, the service provider needs to align with the business objectives and define the success factors to work towards it. The two organizations may have different philosophies toward network infrastructure setup and management, e.g., product stack, traffic flows, security policies, etc. The service provider must combine the business objectives from the different IT philosophies to drive synergies and success.
Stage 1 – Due Diligence
This stage includes an extensive understanding of all aspects of the IT framework, including network, identifying, and understanding the gaps in technology, processes and services, security requirements, and governance mechanisms.
- Ownership and End-of-life statuses of hardware, software, licenses, WAN circuits, and services and contract changes required and associated cost of managing contracts from multiple vendors.
- Detail out potential risks at various stages related to technology, processes, and people.
- Any network activity should be cognizant of regulatory requirements specific to industry & government regulations.
- Determination of the requirements:
-
How many concurrent users will the network need to support?
-
What is the business roadmap? E.g., Are there any new major launches/initiatives planned soon?
-
What type of traffic flows can be expected? E.g., Is it inbound, real-time, and streaming in nature?
-
What should be the room for capacity expansion?
-
What are business priorities and expected Quality of Service? Are you okay with receiving an email 45 seconds later than a distorted video call when the network becomes congested?
-
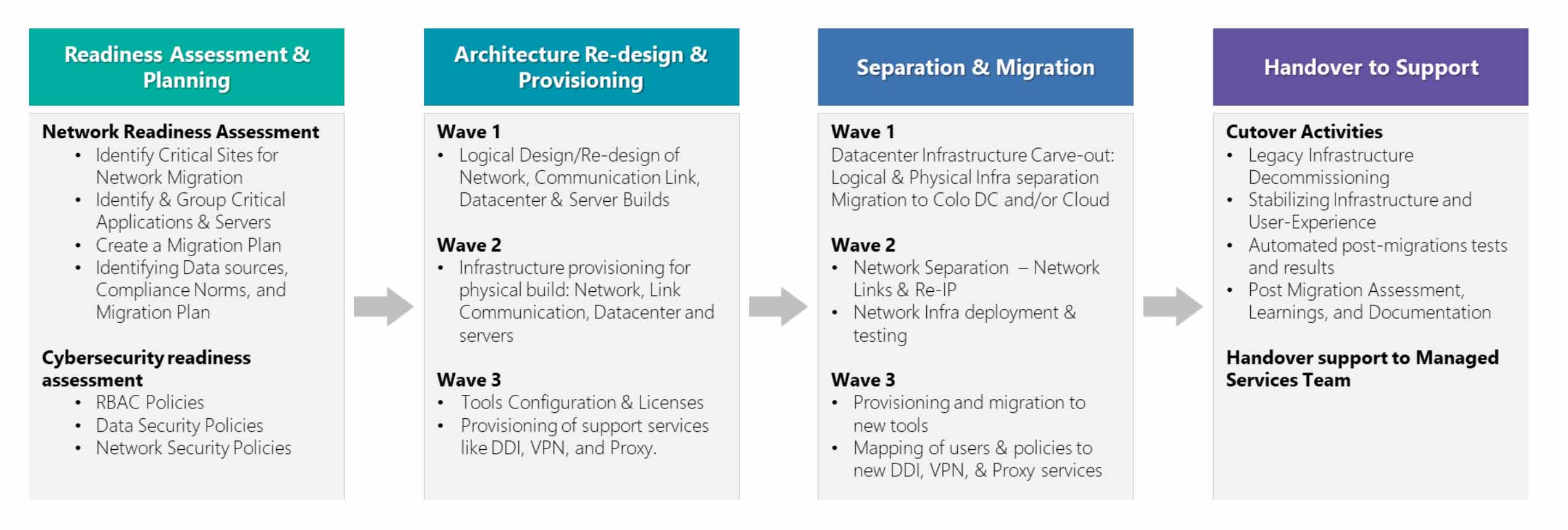
Stage 2 and Stage 3 where the integration planning and execution are undertaken can be further split into 4 different phases as shown in the image below:
Stage 2 – Integration Planning
- Identify all network components and make an inventory of all installed network equipment like Edge Devices, LAN, Wireless, Firewalls, Load Balances, Telephony Equipment, and proxy servers. This information will help to decide as to which network equipment to retain, replace, or refresh based on technical debt.
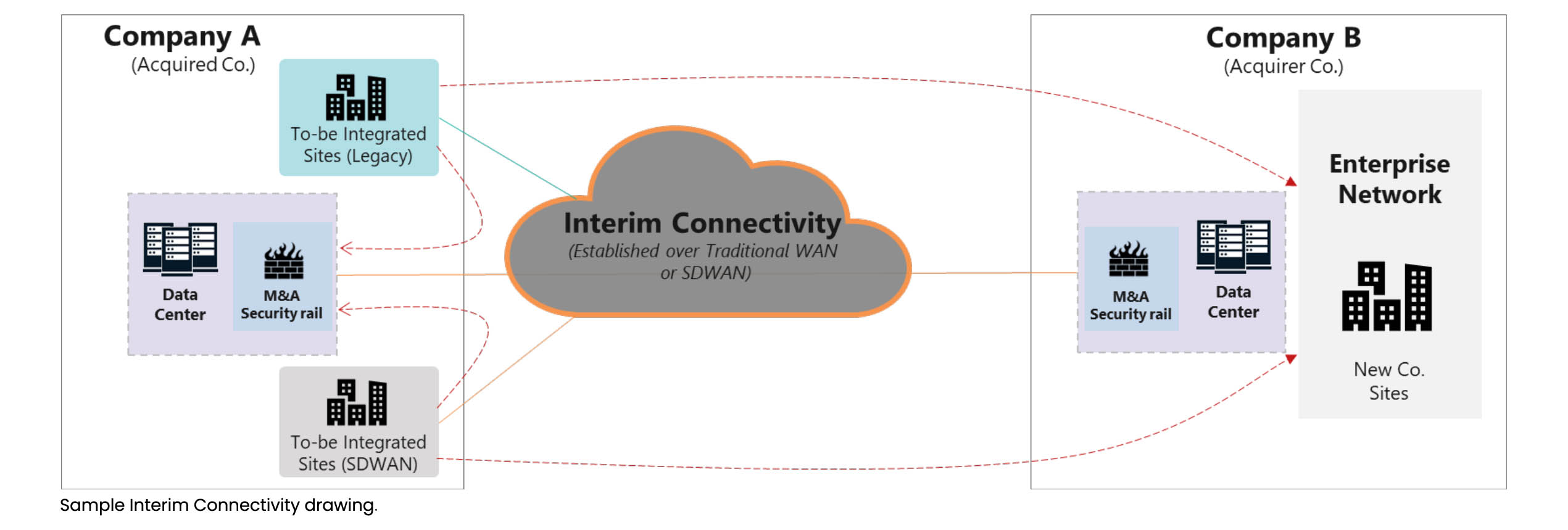
- During the planning phase, a crucial initial step involves preparing for temporary connectivity between the two distinct networks to facilitate essential communication throughout the integration process. This step is essential for achieving a unified view of both networks and comprehending the underlying technology, security protocols, physical locations, design principles, standards, and industry best practices. It allows for gaining insights into the existing state of security, performance, and automation. Additionally, it is imperative to establish security controls and assessments to oversee this interim connectivity.
- Architectural considerations like inter-regional routing, traffic flow from user to cloud applications, user to the internet, user to on-premises applications, etc. to be taken into account while planning to address dissimilarities or incompatibilities due to technology stack, software/licenses, etc., or certain geographies with unique requirements.
- An overview of the IP addressing schema to ensure conflict-free communication in the integrated network.
- Service Levels – Unlike Business-As-Usual (BAU) operations which focus on network uptime, availability, and quality of operations, M&A activity requires different types of services to be measured and benchmarked. A well-defined SLA for the M&A process would be incident-free migration and First Time Right (FTR) deployments.
- Addressing differences & similarities across processes, operating models, and support services like DDI, VPN, and Tools.
- Identifying key stakeholders with clearly defined roles and responsibilities.
- Addressing the risks identified in the due diligence stage and building mitigation strategies to address all business-critical risks, identifying dependencies and the stakeholders to address risks and gaps.
- Well-defined milestones, governance, and communication processes and plans during M&A activities.
Sample Interim Connectivity drawing.
Stage 3 – Integration Execution
Develop a detailed site migration plan based on site criticality, business operations timings, users, and their access requirements. This is to minimize the need for workloads moving across both networks.
This activity requires collaboration with the rest of the IT departments of both organizations and is required to ensure seamless integration of users into the new Active Directory, provisioning mailboxes & collaboration suite, role-based access control, and access to applications and databases. Microland’s holistic solution incorporates the requirements and dependencies of other IT teams.
Stage 4 – Handover to Operations Support
Post-migration, we have an automated UAT testing and Handover to Support (HOTS) process that scans for consistency of configuration, resiliency of the design and performance of the network devices, accuracy of CMDB, and activation of devices in monitoring & management tools. This promotes migrating right the first time to ensure there are no error-led downtimes, re-work & delays in the integration schedule. Due to this automated process, handover is seamless and unambiguous resulting in the timely and appropriate level of support for the customer from Day 0 of migration.
Microland Advantage
Our Mergers and Acquisition initiatives are powered by our platform, Intelligeni NetOps. This platform automatically collects data, including device specifications, bandwidth information, End-of-Life (EoL) details, current configurations, and traffic patterns, from network devices. This automated process significantly expedites the planning phase. Furthermore, the platform serves as a centralized source of accurate information, offering real-time project progress updates. It plays a pivotal role in promoting collaboration among multiple stakeholders, which is essential for any integration or divestiture endeavor. Additionally, it comes equipped with pre-defined configuration templates, reducing the risk of human errors during the migration process.
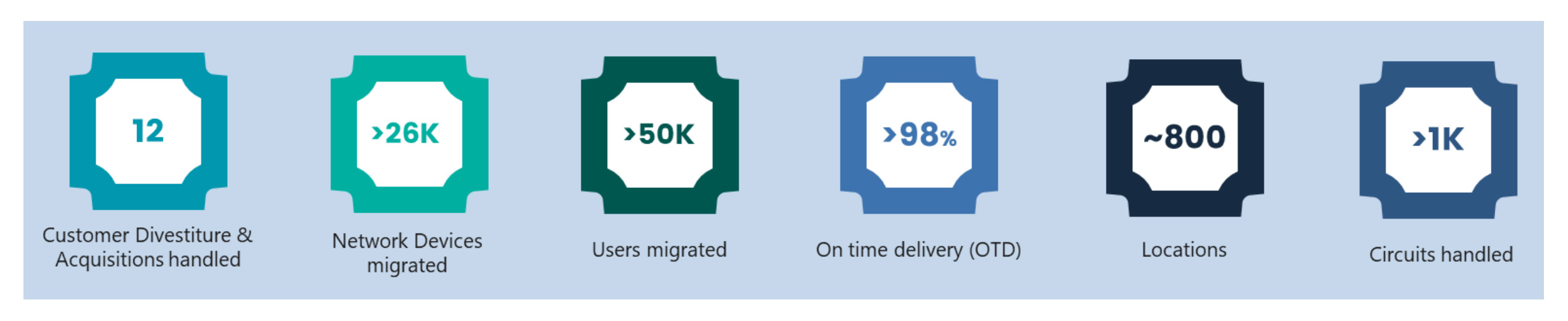
We have helped Fortune 500 customers through large-scale Network and IT Mergers, Acquisitions, and Divestitures across the globe. The combination of our platform approach and global experience minimizes noise during such activities and maximizes the value delivered from Network & IT to meet business goals.