and we will be happy to help
Cyber Transformation Services
Microland has a unique process of delivering cybersecurity transformation services through a comprehensive repository of accelerators, reusable assets, and frameworks for accelerating the adoption of security compliance and cyber-resiliency initiatives, with expertise across industry domains.
Security Transformation Services like design, implementation, integrations of new cyber technologies solutions or replacement of an existing legacy technology.
Our Security transformation services are offered to customers as part of the transition phase of Managed Security services or to our existing security customers. As part of technical services, we established a Content Engineering team that provides continuous content development on playbook development and threat-hunting use cases.
Our approach includes:
1. Right Platform: We advise the right platforms that address specific needs of the enterprise and collaborate with client teams to ensure seamless adoption.
2. Use-case Catalog: We have curated use cases for a multitude of client requirements, challenges, and needs.
3. Plan: We help prepare an execution plan and define implementation roadmap with distinct milestones.
4. Deploy: We provide accelerated deployment as per defined architecture within agreed upon timelines.
5. Configure: We ensure all aspects of the solution are aptly configured for client specific environment.
6. Optimize: Our approach ensures we reduce errors and maximize efficiency.
7. Test: It is our constant endeavor to ensure we meet stringent quality standards that we set for ourselves.
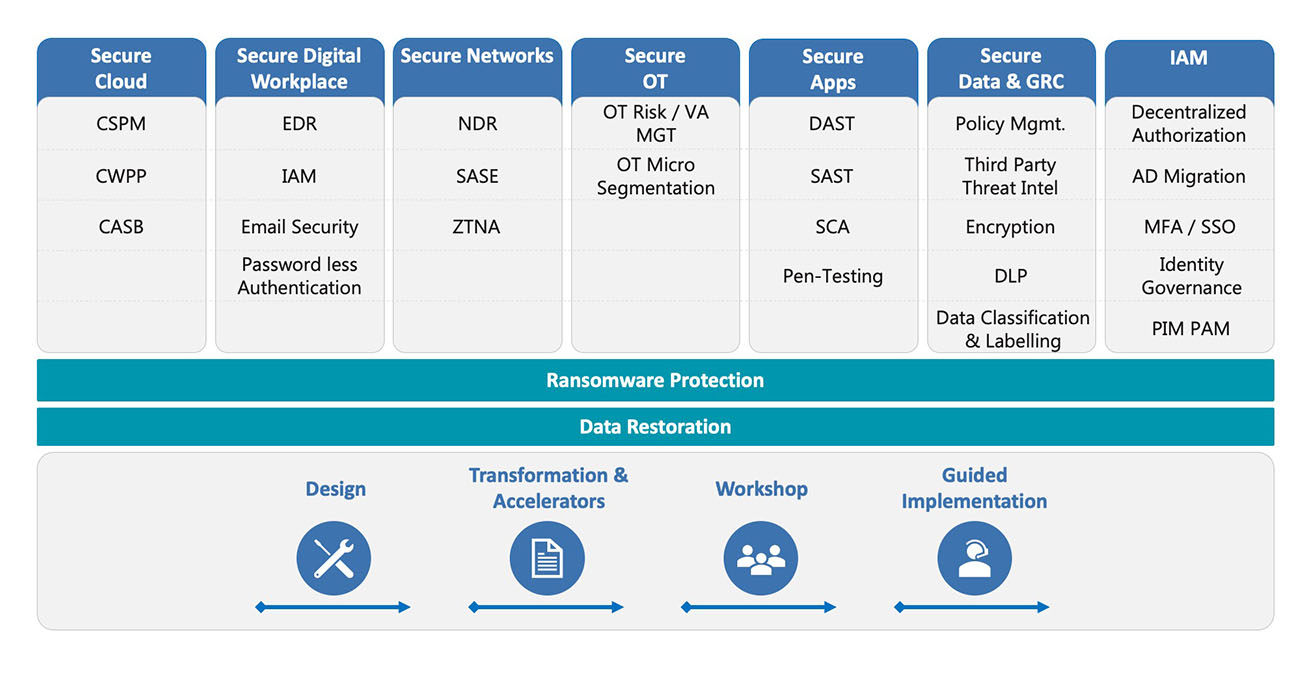
The areas of engagement could range across set of technologies and landscape, as depicted below:
We deliver a rapid transformation using accelerators across the following areas:
As a trusted advisor, we are focused on helping customer on security priorities to accelerate business transformation with:
- Autonomous Response & Orchestration package
- SASE deployment accelerators
- Zero Trust evolved IAM service deployment.
- Password Enterprise program - FIDO standards with cost-effective hardware authentication.
- Rapid Onboard Program MDR
- Continuous Threat Content Service
- OT converged MDR service
- Unified DevSecOps (Code scanning, SAST, DAST, SCA analysis, software supply chain protection mitigation)
We have set up a security implementation process that works towards building a comprehensive repository of accelerators, reusable assets, and frameworks for accelerating customer security compliance as per industry standards.